Main file location for the FBI virus:
C:\Users\"user"\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\"ctfmon.lnk" or "random"
C:\Users\"user"\AppData\Roaming\"random"
C:\Users\"user"\AppData\Local\"random"
C:\ProgramData\"random"
Names found for "random":
- Isass.exe
- yaaiwpoep.exe
- zuoby.exe
- ifgxpers.exe
Registry key location:
HKEY_USERS\S-1-5-21-3167221968-1021630806-270161164-1000\Software\Microsoft\Windows\CurrentVersion\Run\"random"
You might need to use HijackThis to end the Isass.exe , then use task manager to kill it again.
After that delete files;
*This is from personal experience, file could be named differently or located somewhere else.
================Manual Removal #1==============
Normal Antivirus will not work, must remove the virus manually.
** If you don't know what you are doing, don't delete anything
- Re-boot PC in Safe Mode with Networking
- Start Task Manager (Ctrl+Alt+Del)
- Find and stop the process for the scam malware virus
- Open Run
- Type regedit.exe
- Find and delete the following registry entries:
- HKEY_CLASSES_ROOT\personalSS.DocHostUIHandler
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download "RunInvalidSignatures" = "1"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Insternet
- Remove malicious files from the following folders:
- C:\Users\"user name"\appdata\"random"\
- C:\Users\"user name"\appdata\"random"\"random".exe
- C:\Users\"user name"\appdata\"random"\"random".mof
- check also the other folders inside appdata for any random names
Youtube tutorials:
- http://www.youtube.com/watch?v=_gILhDFqm4I
- http://www.youtube.com/watch?v=VYjKMA9gprM&feature=player_embedded#!
================Manual Removal #2==============
1. Open Windows Start Menu and type %appdata% into the search field, press Enter.
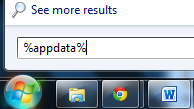
2. Navigate to: Microsoft\Windows\Start Menu\Programs\Startup
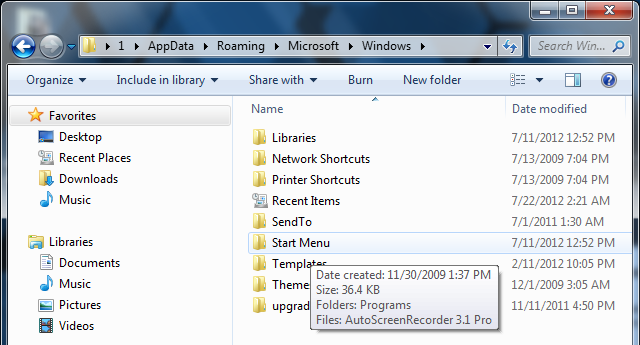
3. Remove ctfmon (ctfmon.lnk if in dos) – this is what’s calling the virus on start up. This is not ctfmon.exe.

2. Navigate to: Microsoft\Windows\Start Menu\Programs\Startup

3. Remove ctfmon (ctfmon.lnk if in dos) – this is what’s calling the virus on start up. This is not ctfmon.exe.
4. Open Windows Start Menu and type %userprofile% into the search field and press enter.

5. Navigate to: Appdata\Local\Temp
6. Remove rool0_pk.exe

7.Remove [random].mof file
8. Remove V.class

5. Navigate to: Appdata\Local\Temp
6. Remove rool0_pk.exe

7.Remove [random].mof file
8. Remove V.class
The virus can have names other than “rool0_pk.exe” but it should appear similar, there may also be 2 files, 1 being a .mof. Removing the .exe file will fix FBI Moneypak. The class file uses a java vulnerability to install the virus, removal of V.class is done for safe measure.
All FBI Moneypak Files:
The files listed above are what causes FBI Moneypak to function. To ensure FBI Moneypak is completely removed via manually, please delete all given files. Keep in mind, [random] can be any sequence of numbers or letters.
- %Program Files%\FBI Moneypak Virus
- %AppData%\Protector-[rnd].exe
- %AppData%\Inspector-[rnd].exe
- %AppData%\vsdsrv32.exe
- %AppData%\result.db
- %AppData%\jork_0_typ_col.exe
- %appdata%\[random].exe
- %Windows%\system32\[random].exe
- %Documents and Settings%\[UserName]\Application Data\[random].exe
- %Documents and Settings%\[UserName]\Desktop\[random].lnk
- %Documents and Settings%\All Users\Application Data\FBI Moneypak Virus
- %CommonStartMenu%\Programs\FBI Moneypak Virus.lnk
- %Temp%\0_0u_l.exe
- %Temp%\[RANDOM].exe
- %StartupFolder%\wpbt0.dll
- %StartupFolder%\ctfmon.lnk
- %StartupFolder%\ch810.exe
- %UserProfile%\Desktop\FBI Moneypak Virus.lnk
- WARNING.txt
- V.class
- cconf.txt.enc
- tpl_0_c.exe
Access Windows Task Manager (Ctrl+Alt+Delete) and kill the rogue FBI Moneypak process. Please note the infection will have a random name for the process [random] which may contain a sequence of numbers and letters (ie: USYHEY347H372.exe).
[random].exe
Remove Registry Values
To access Window’s Registry Editor type regedit into the Windows Start Menu text field and press Enter.


- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\[random].exe
- HKEY_LOCAL_MACHINE\SOFTWARE\FBI Moneypak Virus
- HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Policies\System ‘DisableRegistryTools’ = 0
- HKEY_LOCAL_MACHINE \SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system ‘EnableLUA’ = 0
- HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Internet Settings ‘WarnOnHTTPSToHTTPRedirect’ = 0
- HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Policies\System ‘DisableRegedit’= 0
- HKEY_CURRENT_USER\Software\FBI Moneypak Virus
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run ‘Inspector’
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\FBI Moneypak Virus
- HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Policies\System ‘DisableTaskMgr’ = 0
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Inspector %AppData%\Protector-[rnd].exe
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\WarnOnHTTPSToHTTPRedirect 0
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\ID 4
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\UID [rnd]
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\net [date of installation]
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorAdmin 0
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorUser 0
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\EnableLUA 0
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\Debugger svchost.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe\Debugger svchost.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE\Debugger svchost.exe
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableRegistryTools” = 0
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableTaskMgr” = 0
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “ConsentPromptBehaviorAdmin” = 0
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “ConsentPromptBehaviorUser” = 0
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “EnableLUA” = 0
sources:
